LDAPS
Categories:
CDM Server includes a built-in LDAPS Identity Provider that allows the server to connect securely with your company’s LDAP directory.
This connection uses a connection pool — a single LDAP user account (called the connection account) is used for all LDAP queries from CDM Server.
Note:
All LDAP operations are performed using the permissions of the connection account, not the individual user’s permissions.
CDM Server only needs read access to users and groups under one LDAP main node relevant to CDM workflows.
Prerequisites
Before you begin, make sure you have:
- An existing or new Login Group and Admin User in CDM Server for the setup.
- A valid TLS certificate for your LDAP server (TLS 1.3 is required).
- To allow the CDM-Server to connect to your LDAP server the certificate of the LDAP server must be copied to the root folder of the CDM-Server and named:
cdm-ldaps.pub - The file content needs to be in PEM format.
How Authentication Works in CDM-Server
Once configured, CDM Server uses LDAPS to:
- Verify user credentials with your company’s LDAP server.
- Map LDAP group memberships to CDM Server roles automatically.
This means users are automatically assigned to CDM roles that match their LDAP groups.
Tip:
All users who need CDM Server access must belong to the same LDAP group.
This group must be configured as the Login Group when starting CDM Server for the first time.
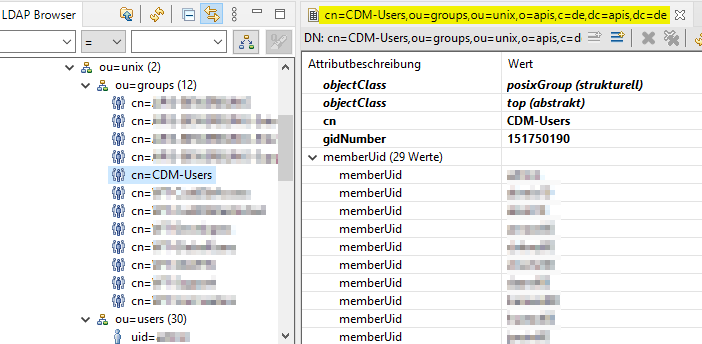
In the image above, the group called CDM-Users includes all users allowed to log in to CDM Server.
Example Configuration
Here’s a sample .env.idp file showing how to configure the ldaps identity provider:
## HELP
# https://get.apis.de/docs/idproviders/ldaps/
## User Management
# Available options: local, azure, ldaps
ID_PROVIDER=ldaps
### User Management -> LDAP
# Only required if ID_PROVIDER=ldaps
# LDAPS server host
AUTH_HOST=
## LDAPS server port
# Change it if you are using a different port
AUTH_PORT=636
## The DN of the user to use to query the LDAP server. This user must have read access to the LDAP server.
# Example: uid=admin,ou=users,o=companyname,dc=domainname,dc=country
AUTH_USER=
## Password for that user
AUTH_PASSWORD=
## User Management -> LDAP -> Internal References
# The full DN of the user in LDAP who is considered admin (This account is needed for server setup)
# Example: uid=admin,ou=users,o=companyname,dc=domainname,dc=country
LDAP_ADMIN_DN=
## The base DN for the LDAP group tree
# Example: ou=groups,o=companyname,dc=domainname,dc=country
LDAP_GROUP_TREE_DN=
## The template for the login name. This is used to construct the full DN of the user to authenticate.
# Must contain {loginName} as a placeholder for the login name.
# Example: uid={loginName},ou=users,o=companyname,dc=domainname,dc=country
LDAP_LOGIN_TEMPLATE=
## USE CUSTOM TLS CERTIFICATE FOR LDAPS (PUBLIC-KEY)
# We always use TLS for LDAP.
# If you have a self-signed certificate for your LDAP instance, set this to true.
# You need to place the custom certificate (public key) in the same directory as your `docker-compose.yml` file (where you have downloaded CDM-Server).
# The certificate file name must be `cdm-ldaps.pub` and it must be in PEM format.
# For a false value, we will attempt to validate the LDAP-Server certificate and it will fail for self-signed/expired certificates.
# Default is false
LDAP_CUSTOM_CERT=false
Inital CDM Server configuration workflow
Before you start CDM Server for the first time, define the admin and group settings in your environment (Docker container).
The following parameters must be set:
| Environment Param | Example Value | Description |
|---|---|---|
| ID_PROVIDER | ldaps | LDAP is used as idprovider |
| AUTH_HOST | openldap.companydomain.country | Network address of the ldap service |
| AUTH_PORT | 636 | The port of the ldap TLS connection |
| AUTH_USER | uid=root,ou=users,o=company,dc=domain,dc=country | User dn of the connection pool user account |
| LDAP_ADMIN_DN | uid=admin,ou=users,o=company,dc=domain,dc=country | Distinguished name of the admin user account |
| LDAP_SEARCH_PATH | o=company,dc=domain,dc=country | Search path containing users and groups in its sub tree |
Next Step
Once you set up.env.idp and login to the system for the first time, you need to do a mapping. Please follow this guide.